
Ecosystem
An Analysis of Interoperability Protocols
There are three different types of interoperability protocols. Let’s have a closer look at each type in the following.

Classification
Of Interoperability Systems
The existing interoperability protocols can be classified within three overarching types based on who verifies transactions. In the following, we will explain each type and have a closer look of the advantages and disadvantages of each system.
Natively Verified Protocols
With the Chain’s Own Validator’s
In a natively verified protocol, the chain’s own validators verify transactions. This means that the underlying chain’s verifiers are responsible for fully validating all data passing between chains. In practice, this is typically achieved by running a light client of a given chain within the VM environment of another chain and vice versa.
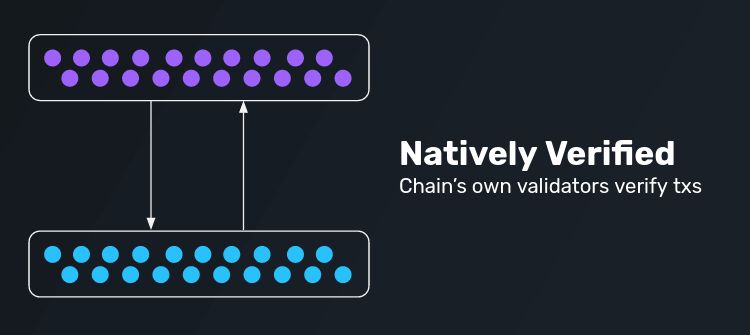
Examples for natively verified protocols are Near RainbowBridge and Cosmos IBC. A special form of this are rollup entries and exits.
Let’s have a look at the advantages such protocols provide but also their inherent disadvantages.
Advantages
Disadvantages
Externally Verified Protocols
Via Third Party Validators
In an externally verified protocol, third party validators verify transactions. Such protocols use an external set of verifiers to relay data and transactions between chains. Typically, these systems are introduced as MPC systems, threshold multisigs, or oracle networks.
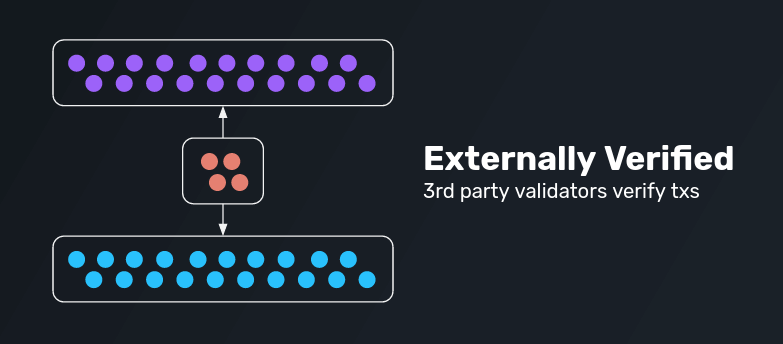
Examples for externally verified protocolsinclude Thorchain, Biconomy, PolyNetwork, and many more.
What are the advantages of such protocols and their limitations?
Advantages
Disadvantages
Locally Verified Protocols
Via Verification Through Counterparties
The last iteration are locally verified protocols in which counterparties verify each other. As such, only the parties that are involved in a given cross-domain interaction verify the transaction. Adopting such a system simplifies a complex problem (n-party verification) into a simpler solution (2-party interactions in which each party verifies only the counterparty). As long as both involved parties are economically adversarial, the system works. However, if there’s an incentive for both parties to collude, funds can be stolen from the broader chain.
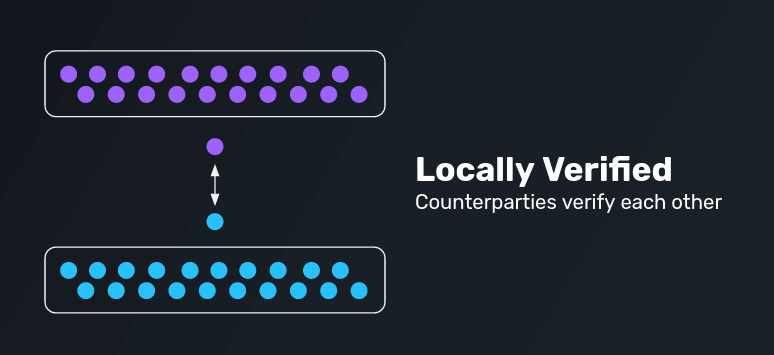
Examples for locally verified protocols include Connext, Celer, Hop, and other simple atomic swap protocols.
What advantages do such protocols provide and what are their disadvantages?

