Ecosystem
Why is Trustless Interoperability Needed?
Let’s have a look at the reasons why trustless interoperability is needed in the first place.

Solution Needed
Cryptoeconomically Secure Bridging Mechanisms
Ethereum’s progression into a multichain/L2 ecosystem and the continued growth of the DeFi space has intensified the need for trustless, cryptoeconomically secure interoperability. In the following, we will take a deep dive into the reasons why such secure bridging mechanisms are needed.
Trustless Ethereum Interoperability
And Why It Is Needed
Without trustless, secure, and decentralized bridging mechanisms, the functionality and growth potential of Ethereum and the entire DeFi sector is limited. In fact, a variety of use cases are unpractical, expensive, and possibly even dangerous to implement in a non-interoperable ecosystem.
The accelerated growth of the DeFi space within the crypto ecosystem has led to the creation of a multitude of new interoperability protocols and bridges.
Considering the dangers of implementing a non-secure bridging mechanism into ones product, developers are confronted with the central question of figuring out which systems are actually cryptoeconomically secure. Similarly, users need to discern which services to use when moving funds between chains – a challenge in the present environment.
What Does “Trustless Interoperability” Mean Exactly?
To better understand why trustless interoperability is needed to accelerate the growth of DeFi while offering the highest level of security, we first need to define what “trustless” actually means in the area of cryptoeconomics.
When it comes to “trustlessness,” cryptographers focus on three simple questions:
To put it simply, decentralized blockchain systems depend on verifiers (i.e. validators or miners) that verify the accuracy of the blockchain’s state. If the verifiers are being corrupted, they can collude to steal user funds by changing the state of the blockchain.
In order to maximize the security of a system, both the diversity and number of verifiers needs to be maximized in combination with the implementation of slashing mechanisms. Combining these three factors allows ecosystems to disincentivize validator collusion and makes corruption attempts excessively costly for malicious third parties.
In practice, establishing such a system is difficult, which is why the ideal scenario is to find a solution that is verified entirely by the existing validator set of Ethereum. At its core, this idea is the central component of L2 and Ethereum’s approach to scalability.
Let’s have a look at such solutions in the following.
Optimistic Rollups
Trustless Two-Way Bridges
The introduction of optimistic rollups (such as Arbitrum and Optimism) within the Ethereum ecosystem has introduced bridges whose transfers are fully secured by the underlying verifiers of Ethereum. This means that a user’s funds transferred through a rollup are as cryptoeconomically secure as funds can possibly be within the blockchain ecosystem.

We can focus next on the question if cryptoeconomic security is also guaranteed for other use cases.
Bridging via External Validators
Third-Party Bridges
Let us now add another layer of complexity by assuming that a user wishes to transfer funds directly between Arbitrum and Optimism without transferring funds to Ethereum first.
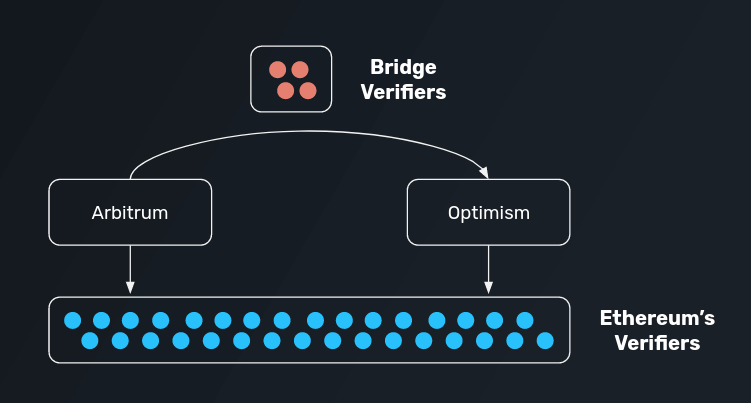
In such a case, a user would have to utilize a bridge protocol between Arbitrum and Optimism.
In practice, this opens up several attack vendors, depending on the system that is utilized to verify transactions: